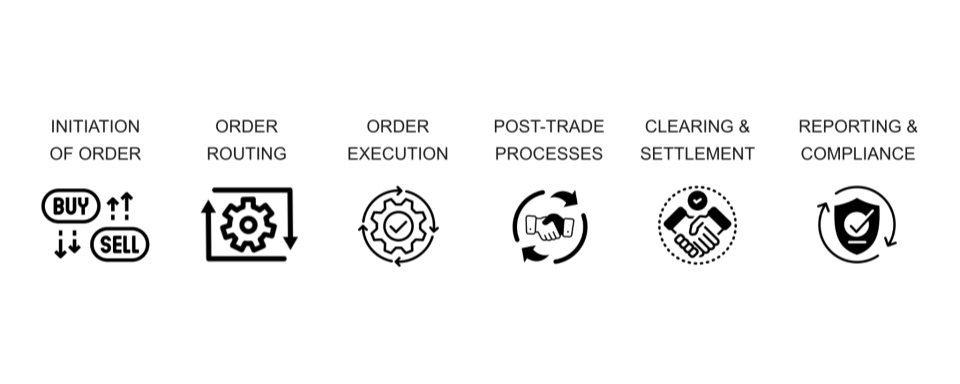
Operation Silent Trader places you at the helm of the Cyber Security Response Team for the London Stock Exchange (LSE), defending one of the world’s largest financial institutions from a highly sophisticated cyberattack.
Your team must safeguard core electronic trading systems while adversaries attempt to manipulate market algorithms and exploit timing discrepancies for profit.
The stakes: continuity of operations, public trust, and the stability of international markets.